If your computer is already fallen prey to CHEATER ransomware, then you must be wondering how to deal with it and save your valuable files. The following guide will tell you everything about the this particular ransomware and show you what need to do to protect against it.
There are a great number of ransomware-type programs on the Internet and CHEATER is one of them. A couple of examples of programs like CHEATER ransomware are Siliconegun, CRYSTAL, and Amber.
The main goal of cyber criminals behind the creation of these programs is to encrypt all the significant files (for example, images, audios, videos, documents, etc.) on the victim’s computer and demand a ransom payment for the decryption.
What is CHEATER Ransomware?
This is a type of high-risk malware infection that is designed to block users’ access to their files stored on the targeted machine by encrypting them. Like other ransomware-type infections, CHEATER also uses the strong RSA and AES algorithms during the encryption procedure and changes the name of the affected files by appending a unique extension.
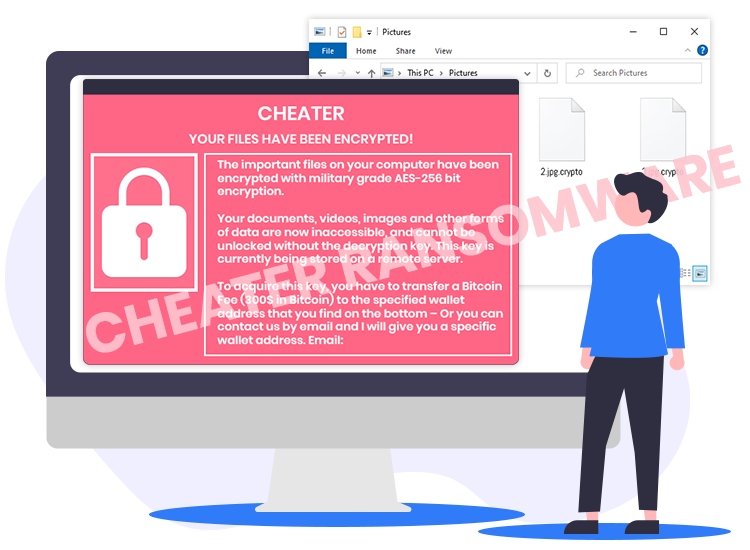
It adds the “.crypto” extension to the end of all the filenames encrypted by it. For instance, the file “music.mp4“, when encrypted by CHEATER, will be renamed into “music.mp4.crypto “.
Soon after the encryption procedure is finished, CHEATER ransomware displays a ransom-demanding message in a pop-up window.
In most cases, the text presented in the pop-up window informs the affected users that all of their stored files have been encrypted and cannot be decrypted without paying a ransom fee to the attackers. It further states that victims first need to contact the creators via the alphateam56@protonmail.com email address in order to receive the specific Bitcoin wallet address.
Important Note: If your computer is already infected by ransomware-type infections, then you’re strongly advised to avoid paying/ contacting the crooks.
Distribution Techniques
Cyber crooks employ a variety of means to download ransomware variants onto the targeted systems. A few of the most common and popular ones are as follows:
- Mal-spam emails
- Intrusive advertisement campaigns
- Drive-by download
- Unofficial software activation tools
- Pornographic sites
- Fake software updaters
- Third-party downloaders/ installers
- Flaws of outdated software versions
How to Remove CHEATER Ransomware from your computer?
Downloading a trusted and competent anti-malware tool with real-time ransomware protection and running a scan is the most efficient way to delete CHEATER ransomware and other next-gen malware threats.


1 Comment