According to experienced cybersecurity experts, Rootiunik ransomware is the newest version of widespread ransomware called ZEPPELIN. Upon infecting the targeted security vulnerable computers, it encrypts all the stored files (e.g., pictures, multimedia, archives, excel workbooks, etc.) and then demands ransom payment for the decryption.
Like Kfuald, CHEATER, Siliconegun, and other data-encrypting malware, Rootiunik ransomware is also created by cyber crooks for the sole purpose of extracting a huge sum of ransom money in the form of Bitcoin cryptocurrency.
Scroll through this article below to learn how to remove this ransomware and protect your computer from such attacks in the future.
What is Rootiunik Ransomware?
Rootiunik ransomware is a malicious program that is designed to encrypt (lock) all types of data stored on a victim’s computer by using powerful cryptographic algorithms.
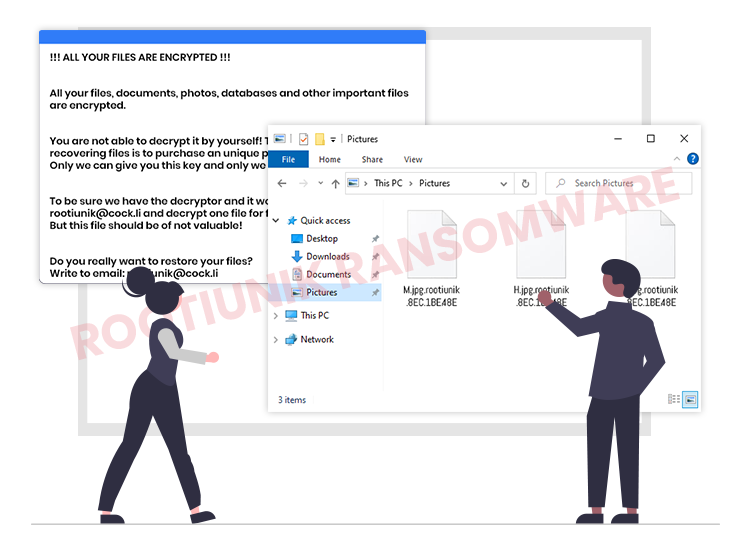
During the encryption process, it renames the encrypted files by adding a special “.rootiunik.[victim’s ID]” extension to the end of all filenames. For example, a file named “1.mp4”, when modified by Rootiunik, would appear something similar to “1.mp4.rootiunik.126-D7C-E67” – following encryption.
Once the encryption is achieved, Rootiunik ransomware creates a special “!!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT” file as its ransom note and drops it into all the folders that contain the encrypted files.
The ransom note informs victims that their data is encrypted and a unique decryption tool/software is necessary to restore it. Moreover, it directs victims to contact the authors of the ransomware through the provided email addresses for further payment-related instructions.
We strongly recommend you not to contact/pay the ransomware authors under any circumstances. These people are only interested in financial benefits.
How Does Rootiunik Ransomware Infect Your Computer?
Ransomware-type infections can infiltrate your computer in many ways. The most common and popular ones are as follows:
- Malicious spam (also known as Malspam)
- Infected URLs and intrusive pop-up advertisements
- Drive-by downloading
- Malicious or porn-related webpages
- Torrent websites
- Fake software updaters
- Removable media devices (such as USB flash drives)
- Unofficial freeware download sites
- Old software bugs/flaws
How to Remove Rootiunik Ransomware from PC?
You can remove the infection from the compromised devices using two methods, i.e., manual and automatic.
Since the manual method includes various removal steps and requires strong technical skills, you are advised to install and use a competent malware removal software for detecting and removing Rootiunik ransomware and other harmful malware infections.


1 Comment