Yajoza ransomware is a type of hazardous computer infection that belongs to the family of ransomware called VoidCrypt. The main purpose of cyber crooks behind this family of viruses is to encrypt files located on the targeted computer and demand ransom payment for decrypting them.
Same as CALVO, LegionLocker 3.0, Mammon, and several other ransomware-type programs, it conducts file encryption on the compromised computer systems within a few minutes after gaining access to it. Read this guide to the end to learn how to completely remove Yajoza ransomware from your computer.
What is Yajoza Ransomware?
As said earlier, Yajoza ransomware is a malicious program that is a part of the VoidCrypt ransomware group. This nasty crypto-virus has been specially designed by a team of cybercrime masterminds to deny users’ access to their crucial files and data (such as work documents, photos, archives, etc.) stored inside the machine and then force them into paying a huge sum of ransom amount to get the decryption key/tool.
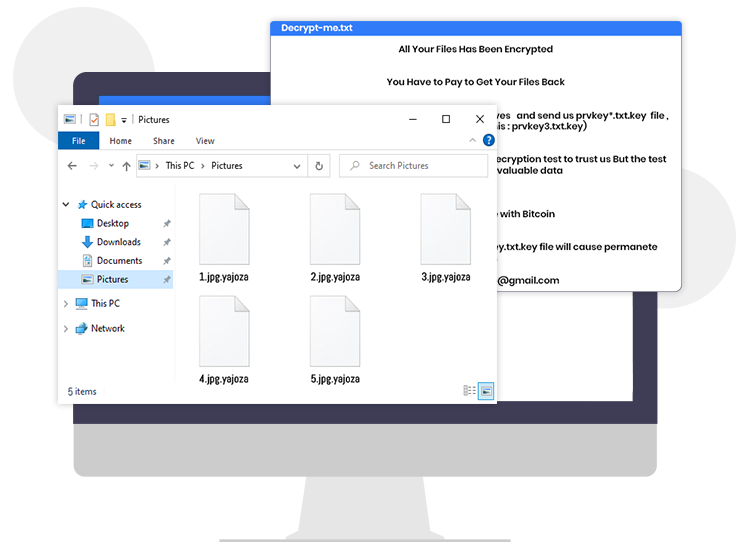
During the encryption process, it modifies the original filename of every encrypted file by appending “.[golpayagob@gmail.com][victim’s unique ID].yajoza” extension. For example, it renames a file named “1.png” to “1.png.[golpayagob@gmail.com][A1B2].yajoza”, “2.png” to “2.png.[golpayagob@gmail.com][A3B4].yajoza”, and so on.
After the encryption process is finished, Yajoza creates a special file named “Decrypt-me.txt” as its ransom note and then drops it into every folder that contains locked files. The text presented in the ransom note (“Decrypt-me.txt”) informs the users that their files have been encrypted using the military-grade cryptography algorithm (AES-256). It further instructs the victims to contact the ransomware developers via the provided email address to get the decryption tool/key and open the locked files.
How Does Yajoza Ransomware Infect Your Computer?
There are numerous methods that can be used by cybercriminals to distribute ransomware, viruses, trojans, or other harmful malware infections in your computer. The most popular ones include:
- Malspam (malicious spam) campaigns
- Intrusive advertisement campaigns
- Untrustworthy freeware download sites
- Cracking tools
- Removable media devices (e.g., USB flash drives)
- Notorious web domains with illegal content
- Outdated software bugs
How to Remove Yajoza Ransomware from PC?
The most convenient and hassle-free way to protect your device and valuable data from crooks, hackers, and identity thieves is to run regular system scans for malware or viruses with some powerful antivirus or anti-malware software.


1 Comment