Cybercriminals are continually developing new attack tools and evolving the sophistication of their attack methods to breach your system defenses. QLKM ransomware is the latest example. This vicious cryptovirus is primarily designed to hold computer files hostage until a ransom is paid by the victim. Keep reading ahead to know everything about QLKM ransomware, what it is, how you get it, and what to do to protect yourself against it.
Do you feel your valuable information is at risk while browsing the web or using your computer? Most people think the same. The significant rise in cyber-attacks around the world has made people aware of how important it is to keep their personal and confidential data protected from external threats.
What is QLKM Ransomware?
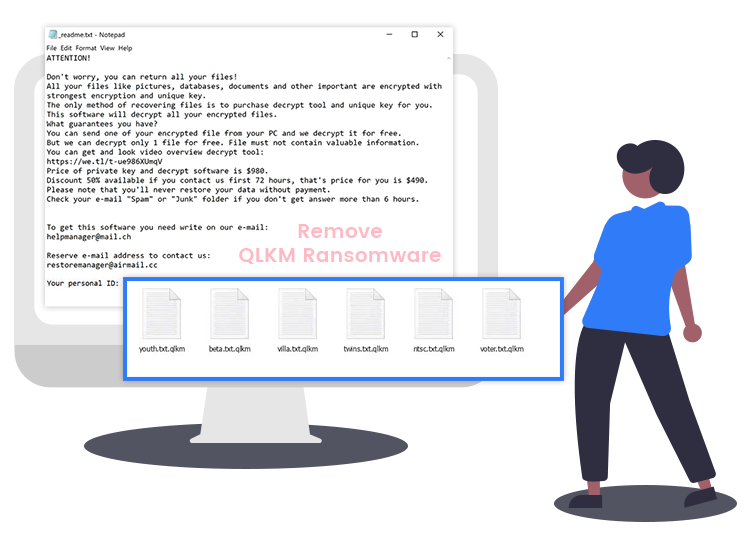
QLKM is a newly detected ransomware-type malicious software that belongs to a ransomware family called Djvu. It is designed to encrypt (lock) all kinds of files (e.g., images, music, archives, work documents, etc.) found on the victim’s computer and demand ransom money in Bitcoin or other cryptocurrencies, in exchange for access to data. Instead of directly locking the victim’s data, it appends its own extension (.qlkm) to the end of all file names. For example, it renames a file named “1.mp3” to “1.jpg.qlkm”, “2.mp3” to “2.jpg.qlkm”, and so on.
Whenever a victim attempts to open any of the compromised files, it displays a ransom-demanding message (“_readme.txt” file), which informs victims of the encryption and provides detailed instructions on how they can regain access to their data by paying a ransom fee. Moreover, it compels victims to establish communication with ransomware creators within the first 48 hours of the attack if they do not want to lose their important files forever.
If the QLKM ransomware has already infiltrated your computer system, we strongly advise you not to communicate with the criminals responsible for the installation of this cyber-threat.
How Does QLKM Ransomware Get Inside the Targeted Computer?
Below are the most common tactics used by cybercriminals to distribute ransomware-type infections.
- Malspam campaigns
- Fake software updating tools
- Third-party freeware download sites
- Questionable web pages that contain malicious script
- Websites that provide adult and porn-related content
- Peer-to-Peer file sharing and hosting networks (e.g., torrent)
- Bugs and flaws of outdated software
How to Protect Yourself against QLKM Ransomware?
The manual threat removal process is quite time-consuming and demands a certain level of technical skills, so we’ll treat it in a follow up article. The best way to protect your computer from QLKM ransomware or any other prevailing malware or virus is by using a dedicated and powerful anti-malware program.

