Gamma is a dangerous piece of malicious software, classified as ransomware. Discovered by a malware researcher named Jakub Kroustek, Gamma ransomware is designed to stealthily infiltrate the targeted system and hold the victim’s personal files stored on it hostage (convert files into an inaccessible format using encryption) until a ransom payment (in the form of cryptocurrencies) is made.
It belongs to the family of ransomware viruses called Crysis. Like other ransomware viruses of this family, it doesn’t provide any information regarding the cryptographic algorithm (symmetric or asymmetric) used to encrypt data, though, successful decryption requires a special key/ tool created individually for each affected user.
Like several other computer users around the globe, if you also been targeted by the Gamma ransomware, then keep reading this blog to find out how you can protect your system against it and save your valuable files.
What is Gamma Ransomware?
This is a type of malware, which poses a serious threat to the security of files stored on your personal computer. If you haven’t heard of ransomware-type of viruses like Gamma before, you should know that they encrypt all types of files stored on a machine and then demands ransom payment (in the form of Bitcoin, Dash, Monero, and other cryptocurrencies) for the decryption.
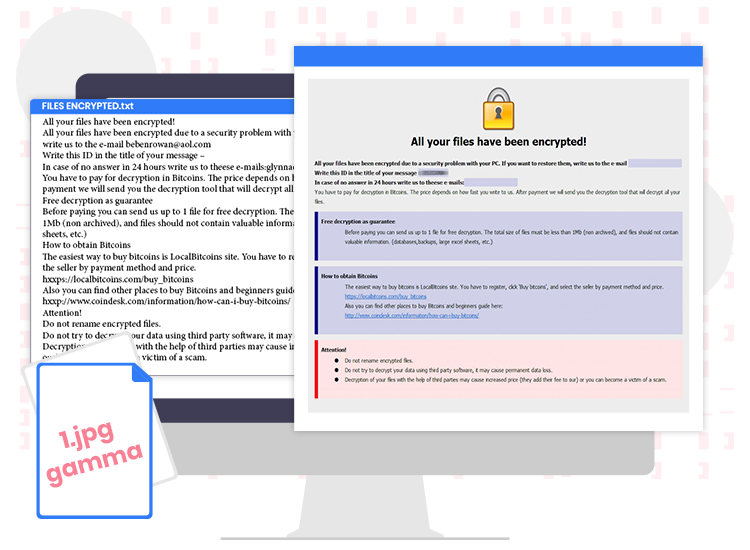
The infection procedure starts by encrypting victims’ files (such as photos, videos, archives, databases, work documents, and others) and changing their filenames by appending “.[bebenrowan@aol.com].gamma” extension. For instance, it renames a file named “1.jpg” to “1.jpg.[bebenrowan@aol.com].gamma”, “2.jpg” to “2.jpg.[bebenrowan@aol.com].gamma”, and so on.
Once the encryption procedure is done, the Gamma ransomware creates its ransom note within the “FILES ENCRYPTED.txt” file, which can be found on each folder containing encrypted files. Like RedDot, MMTA, Venus, and several other ransomware-type viruses, it uses the ransom note to inform victims’ all data has been locked and now they require to contact the ransomware authors via provided email address to initiate the data recovery process.
How Does Gamma Ransomware Infect Your Computer?
Usually, malware infections can be distributed to the targeted systems using the following methods:
- Spam email campaigns
- Exploit kits
- Malicious advertisements
- Unofficial software activation tools
- Scam or illegitimate third-party websites
- Untrustworthy download sources
- Bugs or vulnerabilities of obsolete software
How to Remove Gamma Ransomware?
The simplest and most effective way to detect and remove ransomware infections such as this one is to perform a full system scan using competent and reputable malware removal (anti-malware) tools.


1 Comment