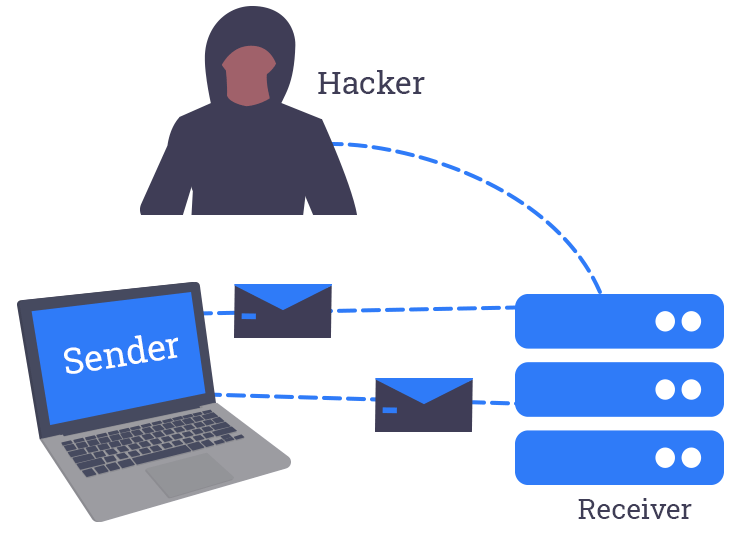
The term spoofing, in cybersecurity, means some kind of impersonation attempt made by cybercriminals pretending to be a name or personality that is easily trusted by the victims. This way, targets willingly reveal confidential information to the scammers.
The scammers mainly pretend to be a legitimate business, a neighbor or friend, a trusted and widely recognized name, or else an innocent party. Stealing data, money, and spreading malware remains the prime goal of spoofing attempts.
How are you spoofed? The most common forms of attack include the following:
- Email, Website or URL spoofing;
- Caller ID or Text message spoofing;
- GPS spoofing
- Extension, IP or ARP (Address Resolution Protocol) spoofing
- DNS Server spoofing
- Facial spoofing
- Man-in-the-middle attacks
Whatever method the scammers use to spoof you, it is incomplete without social engineering techniques. Once the cyber attackers have found a way that can convince you to believe that they are authentic, carrying out the remaining part of the exploitation is a breeze.
All that the scammers now have to do is to expose the naive victims to a malicious payload that will get downloaded on their system. From there on it’s the same age-old game. The malicious program will retrieve confidential data from your system to further exploit you. Now, that we’ve seen what spoofing is, let’s find out about some protective measures.
How to protect yourself against spoofing attacks?
Once you are able to recognize a spoofing attempt, you can try the following security tips to safeguard yourself against it.
- Always exercise immense caution when you are revealing your personal details to anyone.
- Always ensure to turn on the spam filters in the email service you use.
- Don’t respond to unknown or spam calls, and even if you do, don’t divulge important personal information to such callers.
- Never open email attachments or click on links from unsolicited emails.
- Even if you have received an email urging you to open a link for some necessary action, do not comply with the unverified request. Instead, open the website directly on the web browser. This will protect you from getting exposed to the malicious payload that the email link could possibly contain.
- Ensure that your device OS and applications are always up-to-date.
- Install an antivirus program that can protect you against all sorts of cyber threats.
- Alter the Windows settings to display file extensions in folders.
- Avoid downloading any software from unknown websites.
This concludes the topic about what spoofing is and the preventive measures that you can take to protect yourself from such an attack.


2 Comments